NYU Is Targeted by Russian Hackers
According to a report from a website called Recorded Future, a Russian speaking hacker, Rasputin, threatened to sell NYU student and faculty bank routing numbers and social security numbers on the darknet. NYU was one of 60 reported universities and government agencies targeted in the attack.
April 11, 2017
A Russian-speaking hacker calling himself Rasputin threatened to sell NYU student and faculty bank routing numbers, social security numbers and other personally identifiable information on the darknet, according to a report from Recorded Future — a site claiming to search the darknet for potential threats.
According to the report, NYU was one of 60 universities and government agencies targeted in the attack. The Russian hacker gained infamy last year when The Hill reported that they hacked the Elections Assistance Committee and sold high-level credentials to the highest black market bidders. An NYU Information Technology administrator said that NYU handles the financial information, health records and other personal information of over 50,000 faculty and students.
NYU’s Chief Information Officer Len Peters started working at the university in October, and he is one of the key figures tasked with securing the university from cyber attacks. Peters said that while Rasputin did not sell any personal information from NYU, the potential for a crippling attack is highly likely unless combated with military precision.
“My understanding of that particular incident was that it was published that we had vulnerabilities,” Peters said. “But we didn’t find any evidence that we had actually been hacked.”
Recorded Fortune first reported the vulnerabilities and said it attempted to warn institutions before releasing its report. A representative from Recorded Future told WSN in an email that its report focused on the sale of unauthorized access to university networks — and not the actual exfiltration of any private data — reaffirming what Peters said.
Peters said that there are three types of bad actors that are of significant concern for universities: extortionists, hacktivists and non-state actors. Jamyn Shanley, a security analyst at cPanel, a large web-hosting software company, said that the three roles are distinct.
“The extortionist may sell the data back to the victim, the hacktivist may publish it to damage the institution and the non-state actor may use it in other ways to further their own goals,” Shanley said. “But they are all potentially a threat to sensitive information.”
Peters said that since he began working at NYU, there has only been one reportable successful hacking incident. He said that the direct deposit accounts of certain individuals were compromised and subsequently redirected.
“There are literally thousands and thousands of attempts to break into machines on a regular basis,” Peters said. “Sometimes it is to get information that can be monetized on the darknet.”
Shanley said that although his views do not necessarily reflect those of cPanel, he believes larger institutions are susceptible to hackers because there are more potential targets, and that improves the likelihood of success.
Peters said the number of devices used by the NYU community exceeded 120 thousand at last count, and is increasing every day. Shanley said that given NYU’s size, extortionists, hacktivists and non-state actors would likely leverage sensitive personal information to achieve their goals.
Peters said that NYU’s size poses another risk in that a significant number of devices connecting to the network are insecure and are thus more susceptible to hacks. While he said that the university’s public desktop computers are centrally managed and constantly patched with the most recent security updates, this level of security does not apply to students’ personal devices.
“Our confidence level is much higher on public computers because we manage them,” Peters said. “With students, we do not manage [their] devices, so it is really on the student to ensure that those [updates] are occurring.”
He said that due to the high volume of attempts to undermine the network, NYU IT has adopted a risk-based security method. This method, Peters said, is similar to securing a home — fortification starts at the edge with a fence, while more valuable items are protected further inside a safe.
According to Peters, NYU IT created a risk register to determine what information is deemed a higher priority.
“The risk register does two primary things,” Peters said. “It assesses the possibility or probability that that vulnerability could occur and then it accesses the impact if it were to occur and then from that we derive a score. From that [score] we can then prioritize what is most important.”
Peters said during the March 30 University Senate meeting that there are currently 257 active IT risks — 6.4 percent high risk, 43.7 percent medium risk and 50 percent low risk.
Peters said that priorities of this effort shifted toward securing open ports and exploits after this assessment. He said IT security is working to ensure that controls are implemented at the network’s border to monitor its data intake. However, Peters also said exploits, or unpatched machines, are a more elusive threat. To combat this issue, the department is launching a public awareness campaign to educate students and faculty on the need to update their security software.
Shanley said one of the more common and fairly low-tech tactics deployed by hackers is called phishing. It is often implemented through fake links in mass emails, and successful phishing attempts can trick people into sharing their usernames, passwords and other sensitive information. While Peters could not quantify the number of successful scams at NYU, he considers phishing attempts a high risk.
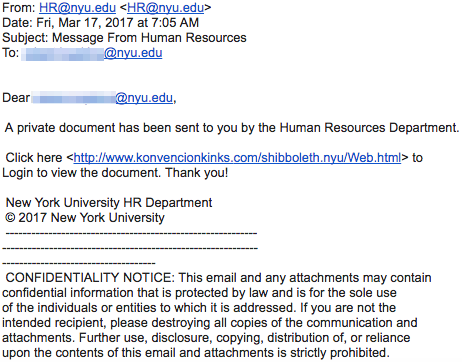
This is a phishing attempt that claims to come from NYU Human Resources. Victims who click on the link are at risk of forgoing their usernames and passwords.
Although electronic-based security is susceptible to cyber attacks, as reported by Business Insider, Assistant Vice President for Strategic Technical Operations at NYU Public Safety Carlos Garcia said the risks are worth the benefits of technology. Therefore, he said the university plans to expand the NYU ID swipe entry currently implemented in buildings such as Bobst Library and the Kimmel Center for University Life.
“If you look at the pros and cons, the pros continue to outweigh the cons,” Garcia said. “What we are trying to do is be proactive and frankly be ahead of the curve in a [security] industry that can sometimes be behind when it comes to technology.”
Email Mack Degeurin at [email protected].